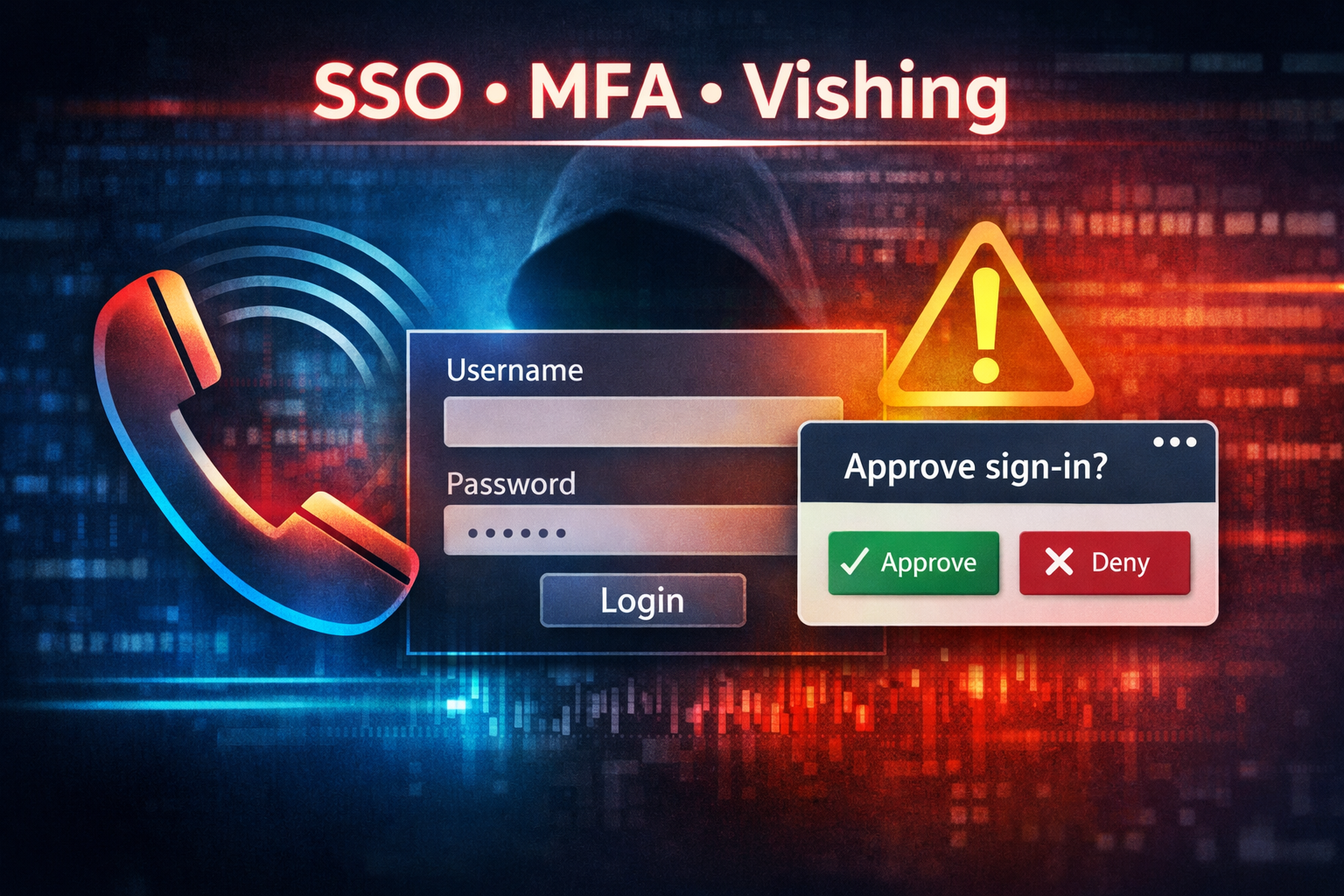
A new wave of real-time voice-phishing (vishing) attacks is targeting enterprise identity systems — particularly single sign-on (SSO) platforms like Okta, Microsoft and Google login portals — to steal credentials and bypass multi-factor authentication (MFA). Criminals are using sophisticated phishing kits that allow attackers to call targeted employees, control what appears in their browser, and sync spoken prompts with authentication challenges in real time, increasing the probability that victims will unwittingly approve MFA prompts or enter codes.
These campaigns have been linked to cybercrime actors using the “ShinyHunters” name, who have claimed responsibility and even posted samples of stolen data online, though formal attribution remains under investigation. Researchers at Mandiant and Okta Threat Intelligence characterize the activity as active and ongoing with malicious domains set up to mimic legitimate SSO pages and extortion attempts already reported by some victims. The attacks underscore the limits of traditional MFA against advanced social engineering and reinforce the need for phishing-resistant defenses and heightened employee awareness.



